The term “cloud computing” is now a familiar one but the full potential of remotely-hosted services is, arguably, yet to be fully embraced in the financial sector. In this article, Farhad Khalilnia, founder and chief executive of , a Geneva and Dubai-based company, addresses some of the issues. Penta specialises in IT provision for the financial sector and industries that require high reliability, data security, ensured business continuity and regulatory compliance. The editors of this news service are grateful for these insights although do not necessarily endorse all the views expressed, and invite readers to respond.
The evolution in IT has resulted in extreme specialisation that reaches into all areas of businesses. The dependence on, complexity and cost of IT services has put unprecedented strain on companies to keep up, and managing the many individual aspects is increasingly difficult.
IT teams need to juggle the demands of staffing, resources, upgrades, compliance, usability and forward-looking strategies to stay competitive and ensure that their IT continues to contribute to business goals and does not become a hindrance. Simultaneously, costs of staffing and technology are squeezing the bottom line.
The recent surge in cloud computing is due the convergence of a number of technologies making it more secure, user-friendly and cost-effective, as well as a mindset shift as people have been exposed to the likes of Hotmail, Dropbox, Facebook and numerous other cloud-based services.
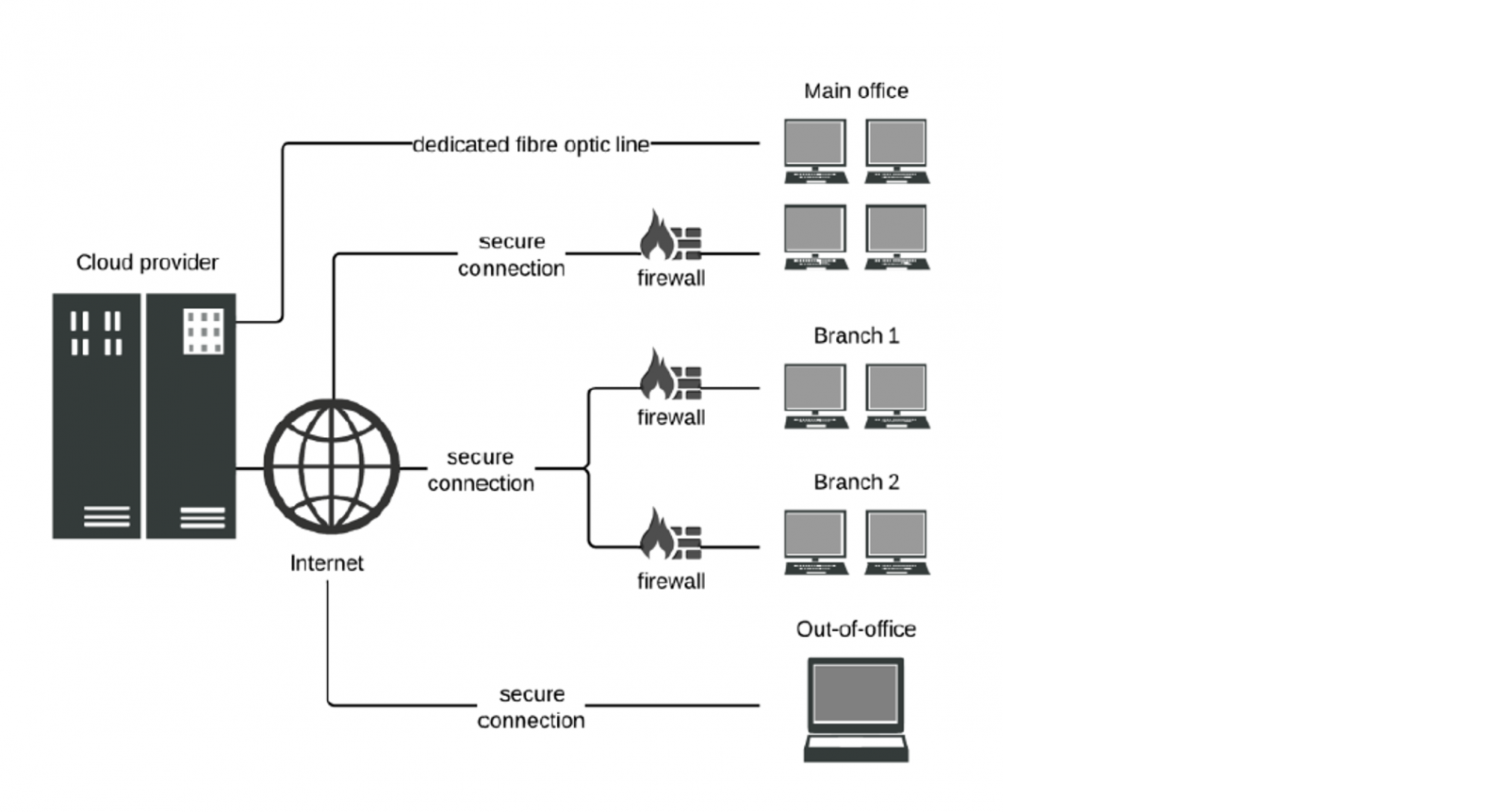
Developments in networking now allow encrypted and secure connections across shared lines, virtual private networks (VPNs) and access to dedicated high-speed point-to-point connections across continents. Storage technologies have evolved to allow shared physical storage space – hard disks – with virtual separation without compromising confidentiality. The computing power – the CPUs and RAM –that runs the applications can also be effectively shared and separated.
Cloud computing means that you can plug into the net, use all of your computing resources as necessary – without concerning yourself with how it is provided – and pay one flat fee based on what you use.
Changing cost structure
The true cost of in-house IT can be elusive - like owning a car. The transparent costs include hardware, software licences and IT staff. However, the financial impact across the equipment life cycle - or total cost of ownership (TCO) - includes lost productivity, purchasing research, migration expenses, electricity and floor space, downtime and recovery, training, insurance, decommissioning and auditing, among dozens of other items. In a cloud set-up, most of these costs are managed by the provider while the business pays one flat predictable fee.
Capital expenditure on IT is reduced to barebones desktops or laptops while the outlay for heavy duty machines, servers, and allowance for future capacity is moved to scalable and predictable operational expenditure. Specialised service providers are able to amortise costs and benefit from economies of scale to an extent which a company, whose core business is not IT, can seldom match.

Regulatory compliance
Regulated industries such as finance are required to meet certain standards in IT and data handling. Certification schemes and legislation vary, but generally involve meeting certain best practices with regards to hardware set-ups, operational processes, and keeping the data in certain jurisdictions. This translates into tight in-house control of IT and cumbersome auditing for regulatory compliance.
Cloud set-ups can meet the most stringent regulatory compliance standards, which poses an interesting advantage over in-house IT – a single audit ensures that all the hosted companies meet the required compliance standards. Again, the costs can be spread across multiple clients.
Opportunities for risk mitigation
With IT so central to modern business, the cost of downtime or data loss can be high, even existence-threatening. A properly run IT department will devote substantial resources to manage these risks.
Data centres allow for easier and more cost-effective risk mitigation than an in-office server. They are purpose built with multiple electricity and internet suppliers, generators, fire suppression systems and biometric access controls among other safeguards.
Virtual threats are managed centrally and for multiple clients simultaneously, meaning more and better equipment and expertise can be dedicated to implementing and monitoring processes, ensuring a quick reaction, and keeping systems and knowledge up to date. Business continuity and disaster recovery are well-developed disciplines that have evolved a lot beyond the traditional backup copy.
Is it secure?
Cloud is a very broad term that refers to many different IT infrastructure set-ups. It is possible to have your own hardware and network connections in a completely private cloud with no physical sharing whatsoever. At the other end of the scale are public clouds where there is little or no control over where, how and with whom your data is stored.
One way to conceptualise cloud security is to consider that the risk of intrusion or data loss is exactly the same on your own computers as it is in the cloud – if the exact same security measures are in place. Both rely on hardware and software for security, and connect to the internet. The question then becomes: can your own computer security set-up match what a dedicated cloud provider can deploy? Like a burglar casing a house and a bank, the weakest target will be compromised first.
Trust, but verify
The one disadvantage of outsourced cloud computing is a loss of control – your data is after all being handled by an external supplier. For that reason, it becomes critical that the custodian of your data plays it straight and transparently, and does not gloss over difficulties. Ensure that they can deliver what is promised, that they are financially secure, and that you can take your data elsewhere if relations deteriorate. The key to successful outsourced cloud implementation is trust – backed by checks, certifications and auditing.
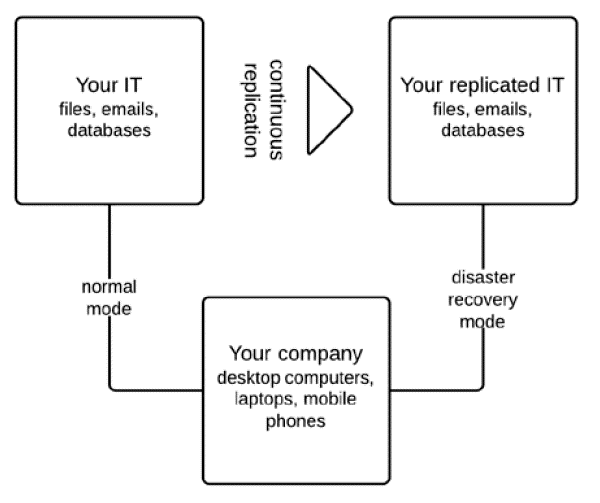
To manage IT risk exposure there are only two factors to consider: data and time. In case of disaster, you can only recover your data from the most recent off-site backup. However, the data that has changed between your most recent backup and the disaster is lost. The time between regularly scheduled complete system backups is called the recovery point objective (RPO) and is the most you are exposed to data loss. Once your system is down, the second variable is the amount of time between a disaster and before your business can be operational again. This is called the recovery time objective (RTO).
Modern systems can back up data instantly – meaning an RPO of zero – even between locations that are geographically separated. A true disaster recovery site should be at least 50 kilometres from the primary site. An RPO of zero is a very high standard and is not always necessary. For example 24 hours or 12 hours is usually more than adequate for many businesses. Equally, the time to recover from a disaster can these days be measured in hours or even minutes, and is usually dictated by the human reaction time – the time it takes to establish that a disaster is underway – rather than technical limitations. Again, very short RTOs are not required in every business and for all systems.

IT outsourcing in various forms is often referred to as XaaS, or X-as-a-service. Network-as-a-service (NaaS) is the most basic type of outsourcing, familiar to most as telephones, internet connections and perhaps the local network.
Infrastructure-as-a-service (IaaS) is also a familiar. For example, a local IT company will install computers and servers in your office and dispatch technicians for maintenance. In a cloud set-up, there is still a need for basic desktop computers or laptops. However, these serve only to connect to the off-premise data centre, sending keyboard strokes and mouse clicks one way and receiving the monitor image the other way. Today’s high-speed connections make the interaction seamless and office computers only need basic specifications as the real work takes place in the cloud. Platform-as-a-service (PaaS) dispenses with the need to buy and maintain your own operating systems and databases. The necessary platforms are run from a data centre and delivered on a continuous basis—including updates, security patches, new versions and so on.
Software-as-a-service takes the concept a step further and delivers the end-user applications—the actual software used to work such as Microsoft Office and custom or off-the-shelf programmes.
